 It has been my observation since the first references to big data analytics were made that it truly holds the promise of ensuring we derive greater insights into behavior even as we gain fresh awareness of patterns and trends that determine success, or otherwise, in business. This is particularly pertinent to those relying on HP NonStop systems for their transactional processing that is almost always involving interaction with customers, in realtime. Nothing is more relevant than being able to modify a product or service offering to a customer when they are right in front of you, having their payments processed.
It has been my observation since the first references to big data analytics were made that it truly holds the promise of ensuring we derive greater insights into behavior even as we gain fresh awareness of patterns and trends that determine success, or otherwise, in business. This is particularly pertinent to those relying on HP NonStop systems for their transactional processing that is almost always involving interaction with customers, in realtime. Nothing is more relevant than being able to modify a product or service offering to a customer when they are right in front of you, having their payments processed.
However, this potential beneficial insight doesn’t end with just the transaction, but rather is becoming just as important a consideration when the same big data analytics is turned inwards and turns the spotlight onto the data center itself. In today’s enterprise data centers have become very complex, with a myriad compilation of heterogeneous systems and components such that it’s not always obvious where the “doors have been left open” or when a data center is being probed by those intent on causing malicious damage, the bad guys, as we so often read about them perpetrating some of the most outrageous breaches of our personal and financial information.
Detecting Big Data footprints in realtime to prevent breaches.
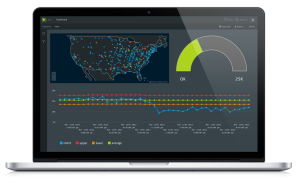
Solutions monitoring products, those watching over the systems, networks and applications we run, are turning to big data in order to raise the alarm at the earliest possible moment. A door left open (where manufacturer’s logon ids / passwords haven’t been changed, for instance) or a file left unencrypted or un-tokenized, will always be a temptation for the bad guys, but they rarely find these on their first attempt. And as they begin their penetration of a data centers defenses, they leave a footprint that often can only be seen by the best of realtime data analytics processes.
At WebAction, Inc. they understand that it is “increasingly difficult to match the speed and level of sophistication of your customers’ experience. With that in mind, your competitive advantage lies in correlating information more quickly.” When it comes to monitoring and in particular, watching for attacks as soon as they start, the speed and level of sophistication exhibited by your bad guys demands the same quickness in correlating information from the many systems and applications running within the data center. These observations found their way into an upcoming article in the HP bimonthly magazine, The Connection, where WebAction Cofounder and EVP, Sami Akbay, provided his own insights into the value WebAction provides those charged with monitoring all that flows through the data center.
Stream analytics and NonStop for actionable insights.
“What WebAction is particularly good at providing is ‘actions’ generated whenever selected criteria have been met,” said WebAction Cofounder and EVP, Sami Akbay. “We know that security is a priority for many enterprises and it’s a complex situation to effectively monitor – there are so many moving parts in a data center these days, with systems spanning many generations – where even the simplest device possesses incredible intelligence. As we provide an end-to-end platform with WebAction that delivers actionable insights from Big Data (the sum of all event logs being generated 24 X 7) we are well-positioned to catch the slightest variance that in and of itself may be the first clue any enterprise has that it’s under attack.”
As Canada just found out and acknowledged this past week critical databases, including those used by their own spy force, were attacked. Not hacked, but attacked, and this is the nature of breaches revealed of late. So it’s becoming widely understood that the speed and level of sophistication of your bad guys demands matching quickness in correlating information not just to catch what has happened so as to see the very first steps being taken, whereby actions can be taken as near to realtime as the technology allows. This, most of all, is perhaps a capability of big data and big data analytics that might be overlooked by some enterprises, but for those aware of the possibilities that can come with turning big data analytics loose on the data center itself may just be those who are able to more quickly deflect those efforts to harm their credibility, even before it makes the evening news.