Using vaults
Vaults provide secure storage for any sensitive information, such as passwords, tokens, or keys. You can use a vault to secure the value of any property in Striim. Vaults store sensitive information as encrypted key-value pairs. TQL can use the keys as variables, keeping the cleartext value secured even from the developer.
Note
Striim automatically encrypts values when the property type is com.webaction.security.Password (see Encrypted passwords), but if desired you may specify vault keys for those values.
Striim's native vault encrypts the values using AES-256 and stores key-value pairs in Striim's metadata repository.
Alternatively, you may store key-value pairs in an Azure Key Vault, CyberArk Vault, Google Secrets Manager, or Hashicorp Vault's KV Secrets Engine Version 2. Striim does not support Azure Key Vault endpoints in Azure Government, Google Secrets Manager endpoints in Google Cloud for Government, or HashiCorp Vault endpoints in AWS GovCloud, Azure Government, or Google Cloud for Government.
Tip
When handing off applications from development to QA, or from QA to production, create vaults with the same name in different namespaces. If vaults' entries have the same names but different values, the applications can use different connection URLs, user names, passwords, keys, and so on with no need to revise the TQL.
Striim native vaults
To create a Striim native vault:
CREATE VAULT <vault_name>;
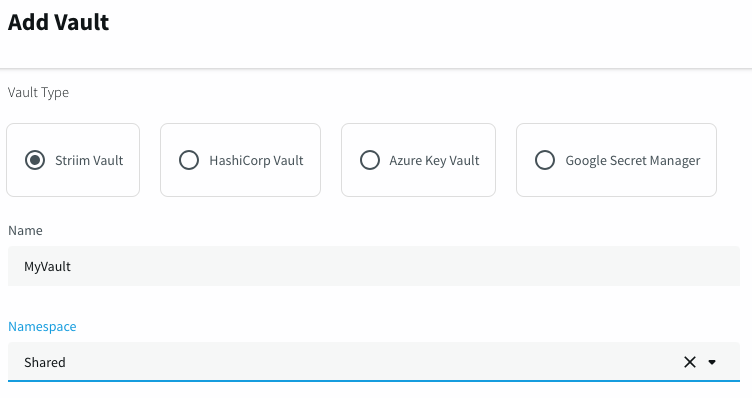
Or in the web UI, select Manage Striim > Vaults > Add Vault, enter a name for the vault, select the namespace in which to create it, and click Confirm:
To add an entry to a Striim native vault, the syntax is:
WRITE INTO <vaultName> ( vaultKey: "<key>", vaultValue : "<value>", [ valueType: "FILE" ] );
If valueType: "FILE" is specified, value must be the fully-qualified name of a file accessible by Striim. (The file can be deleted after the vault entry is created). For example:
WRITE INTO MyVault ( vaultKey: "MyKey", vaultValue: "/opt/striim/UploadedFiles/myfile.txt", valueType: "FILE" );
Otherwise, value must be a string. For example:
WRITE INTO MyVault ( vaultKey: "MyKey", vaultValue: "12345678" );
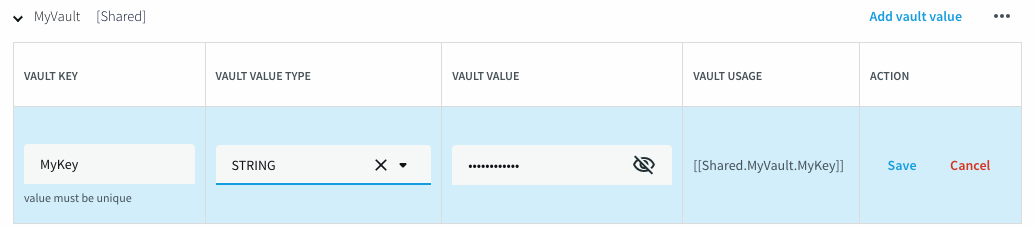
Or in the web UI, select Add vault value, enter a name for the vault key, select STRING or FILE as the value type, enter the string or select the file, and click Save.
Azure Key Vault
To create a vault component that makes an existing Azure Key Vault key available for use in Striim:
CREATE VAULT <vaultName> USING VAULTSPEC ( VaultType: "AZUREKEYVAULT", ConnectionURL: "<connection_url>", ClientID: "<Application (client) ID>", ClientSecret: "<Secret ID>", TenantID: "<Directory (tenant) ID>" );
The values to specify are:
ConnectionURL: from the Overview page for your Key Vault.
ClientID: the Application (client) ID from the Overview page for the Azure Active Directory application with read permission on the vault (applications are listed on the Active Directory "App registrations" page).
ClientSecret: The Value from the "Certificates & secrets" page for the Active Directory application with read permission on the vault.
TenantID: the Directory (tenant) ID from the Overview page for the Azure Active Directory application with read permission on the vault.
You cannot add a key to an Azure Key Vault in Striim. See Microsoft's Add a secret to Key Vault for instructions on adding keys.
CyberArk Vault
To create a vault component that connects to CyberArk Central Credential Provider (CCP) for use in Striim:
CREATE VAULT <vault_name> USING VAULTSPEC (
VaultType: "CYBERARKVAULT",
ConnectionURL: "<CCP_AIM_WebService_URL>",
AppID: "<application_ID>",
SafeName: "<safe_name>",
CertificateName: "<path_to_certificate_file>",
CertificatePassword: "<certificate_password>",
CertificateType: "{PKCS12|JKS}",
SSLVerification: "{true|false}",
ConnectionTimeout: "<timeout_ms>",
ReadTimeout: "<timeout_ms>"
);The values to specify are:
ConnectionURL: the CyberArk CCP AIM WebService URL (for example,
https://server.example.com/AIMWebService).AppID: the CyberArk Application ID configured for CCP authentication.
SafeName: the CyberArk safe containing the accounts to access.
CertificateName: (optional) the path to the client certificate file for mutual TLS authentication. Required for CCP endpoints that enforce mutual TLS.
CertificatePassword: (optional) the password for the client certificate keystore. Required when CertificateName is specified.
CertificateType: (optional) the certificate keystore type, either
PKCS12for PFX files orJKSfor Java KeyStore files. Defaults toPKCS12.SSLVerification: (optional) set to
trueto enable SSL certificate verification. Defaults tofalse.ConnectionTimeout: (optional) connection timeout in milliseconds. Defaults to 30000.
ReadTimeout: (optional) read timeout in milliseconds. Defaults to 60000.
For example, using a PKCS12 certificate:
CREATE VAULT MyCyberArkVault USING VAULTSPEC ( VaultType: "CYBERARKVAULT", ConnectionURL: "https://cyberark.example.com/AIMWebService", AppID: "Striim_App", SafeName: "Striim_Safe", CertificateName: "/opt/striim/certs/client.pfx", CertificatePassword: "certpassword", CertificateType: "PKCS12", SSLVerification: "true" );
CyberArk vault references use a different syntax than other vaults. Because credentials are stored in CyberArk accounts, you must specify both the account name and the key name separated by a colon:
Password: '[[MyCyberArkVault.oracle_account:password]]'
You cannot add credentials to CyberArk in Striim. See the CyberArk documentation for instructions on managing accounts in your CyberArk safe.
Google Secret Manager
To connect with the Google Secrets Manager, use Google's provided API. Authenticate to the API using the service key. The account must have the Secret Manager Secret Accessor role.
To create a vault component that makes an existing Google Secret Manager secret available for use in Striim:
CREATE VAULT <vault_name> USING VAULTSPEC ( VaultType: "GOOGLESECRETMANAGER", ProjectID: "projectIDExample", serviceAccountKeyPath: "serviceAccountKeyJsonFormat" );
You cannot add a secret to Google Secret Manager in Striim. See Secret Manager > Documentation > Guides > Create and access a secret using Secret Manager for instructions on adding secrets to Google Secret Manager.
Vault by Hashicorp
To create a vault component that makes an existing Vault by Hashicorp secret available for use in Striim:
CREATE VAULT <vaultName> USING VAULTSPEC ( VaultType: "HASHICORPVAULT", AccessToken: "<rootToken>", ConnectionURL: "<connection_url>", Port: "<port>", EngineName: "<name>", PathToSecret: "<path>", AutoRenew: "{true|false}", -- default value is false AutoRenewIncrement: "<interval>", AutoRenewCheckPeriod: "<interval>"
);For example, without auto-renew:
CREATE VAULT myvault USING VAULTSPEC ( VaultType: "HASHICORPVAULT", AccessToken: "**************************", ConnectionURL: "https//198.51.100.20", Port: "8200", EngineName: "secret", PathToSecret: "my-secret" );
Alternatively, to enable auto-renew:
CREATE VAULT myvault USING VAULTSPEC ( VaultType: "HASHICORPVAULT", AccessToken: "**************************", ConnectionURL: "https//198.51.100.20", Port: "8200", EngineName: "secret", PathToSecret: "my-secret", AutoRenew: "true", AutoRenewIncrement: "7d", AutoRenewCheckPeriod: "1d" );
AutoRenewIncrement specifies the time-to-live (expiration) of the tokens (see Token Management).
AutoRenewCheckPeriod controls how often Striim will check to see if the current token should be renewed.
To ensure that your token is always valid, the AutoRenewCheckPeriod interval must be shorter than the AutoRenewIncrement interval.
Valid interval unit indicators are
msfor milliseconds,sfor seconds,mfor minutes, andhfor hours, anddfor days.
You cannot add a secret to Vault by Hashicorp in Striim. See Hashicorp's Vault Documentation for instructions on adding secrets to KV Secrets Engine Version 2.
Using vault keys as variables in TQL
Specify vault entries in TQL adapter properties with double square brackets. For example:
Username: '[[myvault.myusername]]', Password: '[[myvault.mypassword]]',
For CyberArk vaults, you must specify the account name and key name separated by a colon:
Password: '[[myvault.account_name:key_name]]'
If you are using an Azure Key Vault, CyberArk Vault, or Hashicorp Vault and the property expects a value to specify a file, indicate that as follows:
ServiceAccountKey: '[[myvault.my-sa-key, "FILE"]]'
, "FILE" is not required in TQL when using Striim's native vault.
Other vault commands
Note
After entering an ALTER VAULT command, any Striim applications that use that vault must be restarted to update the value.
ALTER VAULT <vault_name> SET ( vaultKey: "<key name>", vaultValue : "<new value>");
For a Striim native vault, changes the value of the specified key. (You cannot change key values for third-party vaults in Striim.)
ALTER VAULT <vault name> (connectionURL: "https://<new connection URL>");
For a third-party vault, changes the connection URL.
ALTER VAULT <vault name> (ClientSecret: "https://<new client secret>");
For an Azure vault, changes the Secret ID.
ALTER VAULT <vault name> (AccessToken: "**************************");
For a Hashicorp vault, updates the access token.
DESCRIBE <vault_name>;
Returns a description of the specified vault component.
DROP VAULT [<namespace>].<vault_name>;
For a Striim native vault, deletes the vault and all its entries.
For a third-party vault, makes it inaccessible by Striim, but has no effect in Azure Key or Hashicorp vaults.
LIST VAULTS;
Returns a list of vaults usable by the current user.
READ ALL FROM <vault_name>;
Returns the encrypted values for all keys in the vault.
READ FROM <vault_name> WHERE vaultKey="<key>";
Returns the encrypted value for the specified key.