Managing control plane alerts in Striim Cloud
Striim Cloud supports a robust alerting system at the control plane (Striim Cloud Console) level, enabling proactive monitoring of service lifecycle events and service health status across the Striim Cloud environment. This complements existing data plane alerts that focus on application and server-specific conditions.
Striim supports two distinct types of alerts:
Data plane alerts: alerts from your Striim Cloud instance, for example, application errors and CPU thresholds. See the Getting alerts about servers and applications.
Control plane alerts: alerts about the health and lifecycle of services at the Striim Cloud Console level. This topic covers control plane alerts.
Overview
With control plane alerts in Striim Cloud, you can:
Monitor real-time health and lifecycle changes across services
Configure alert rules based on defined conditions
Send notifications to relevant stakeholders
Review alert history for audit and incident analysis
Manage alert access through role-based permissions
Alerts are organized into two primary categories:
Service Lifecycle: Alerts triggered by changes in the lifecycle of services (e.g.,
Start,Stop,Failure).Service Health: Alerts indicating service availability or performance degradation. States include
Healthy,Degraded,Critical,Offline.
Accessing alerts and alert configuration
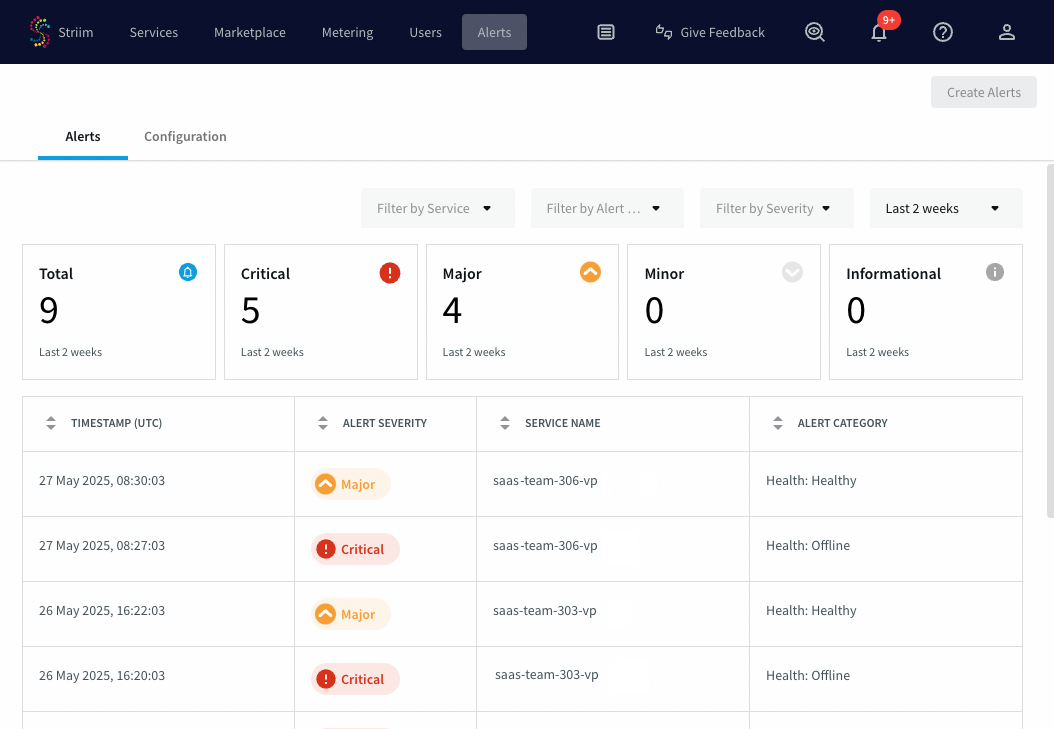
You can view recent alerts and manage alert rules directly in the Striim Cloud UI.
Navigate to the Alerts section in the Striim Cloud UI.
In the Alerts tab, review all triggered alerts from the past two weeks. Each alert includes the timestamp, severity, and associated service.
Use filters to narrow by service, category, or severity.
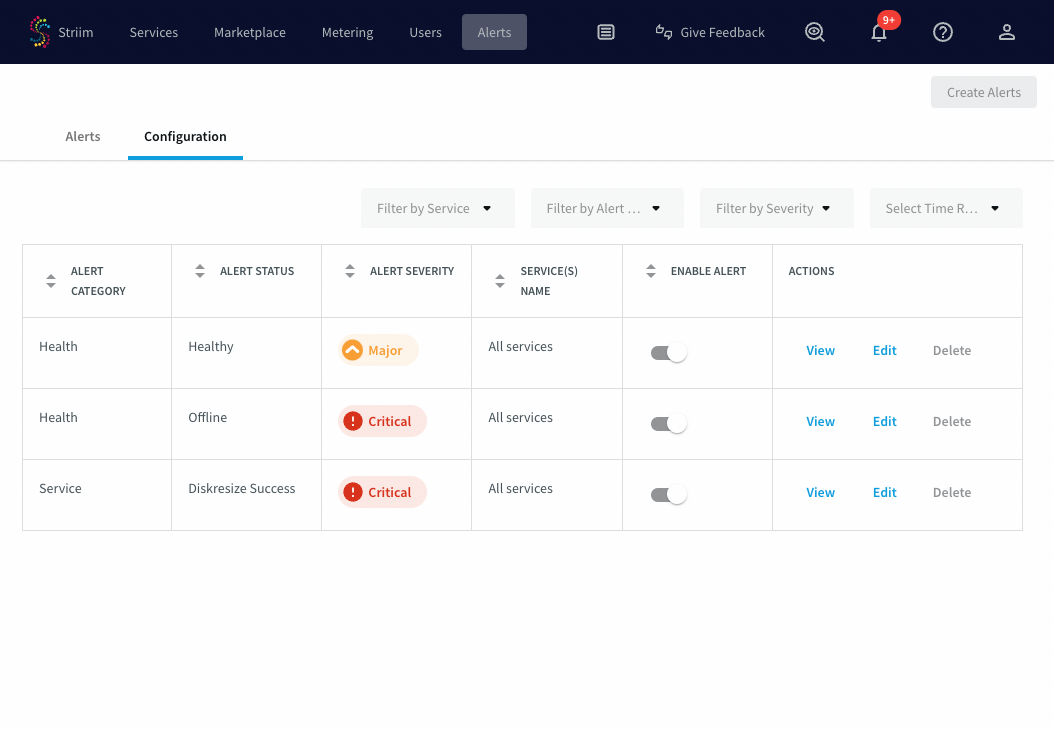
Switch to the Configuration tab to manage alert rules.
Creating and configuring alert rules
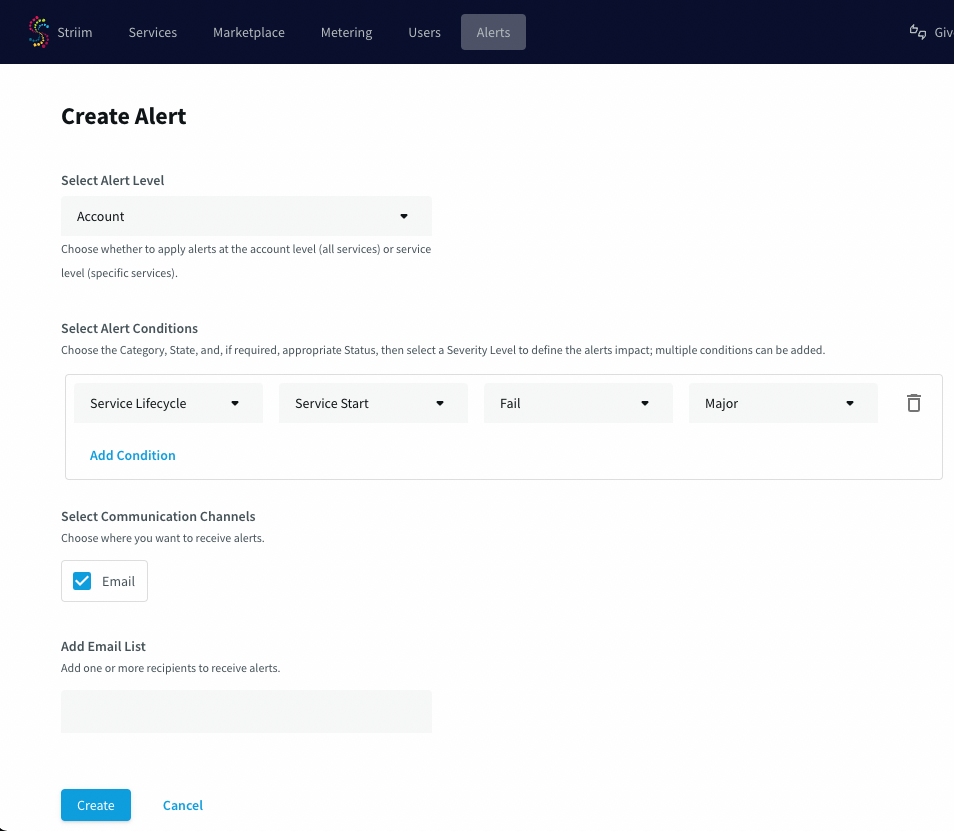
To create a new alert:
Navigate to Configuration > Create Alert.
Complete the following fields:
Select Scope:
Account-Level: Applies to all services in the tenant
Service-Level: Applies to selected services only
Define Conditions:
Category: Select
Service HealthorService LifecycleState: Choose a specific state that would trigger the alert (e.g.,
Creatingfor service lifecycle,Offlinefor service health)Status: Optional; varies by category and state
Severity: Choose from
Critical,Major,Minor, orInformationalUse Add Condition to combine multiple triggers in a single rule
Notification Channel:
Select Email
Add one or more recipients (individual addresses or distribution lists)
Alert notifications
When an alert is triggered:
An email notification is sent to the configured recipients and is also logged into the alert history.
Viewing alert history
To explore past alerts and understand trends:
Navigate to the Alerts tab.
Use filters to narrow the alerts by:
Time range
Alert category
Service name
Alert Severity
Review metadata such as:
Trigger timestamp
Breach conditions (Alert Rule)
This view helps teams analyze root causes, improve alerting rules, and monitor system health over time.
Roles and permissions
Control plane alert configuration and visibility follow role-based access control (RBAC):
Role | Permissions |
|---|---|
Admin | Full access to create, edit, and assign alert rules |
Service Admin | Create, edit, and assign alerts for services they manage |
Developer | View alert logs only; cannot modify alerts |
Viewer | View alert logs only; no edit permissions |
Only Admin and Service Admin roles can modify alert configurations or manage recipients.
For more information on the individual alert permissions, see Managing permissions and roles in Striim Cloud.