Managing activity logs
Activity logs are accessed by selecting the Activity log icon in the upper-right corner of the navigation bar. The activity log provides visibility into both account-level and service-level audit events, offering users a detailed record of interactions across the platform. These logs support operational transparency, help with troubleshooting and security reviews, and allow teams to monitor system usage and changes over time. Activity logs are available only for services running Striim Cloud version 5.2.0 or later and are retained for a minimum of one year.
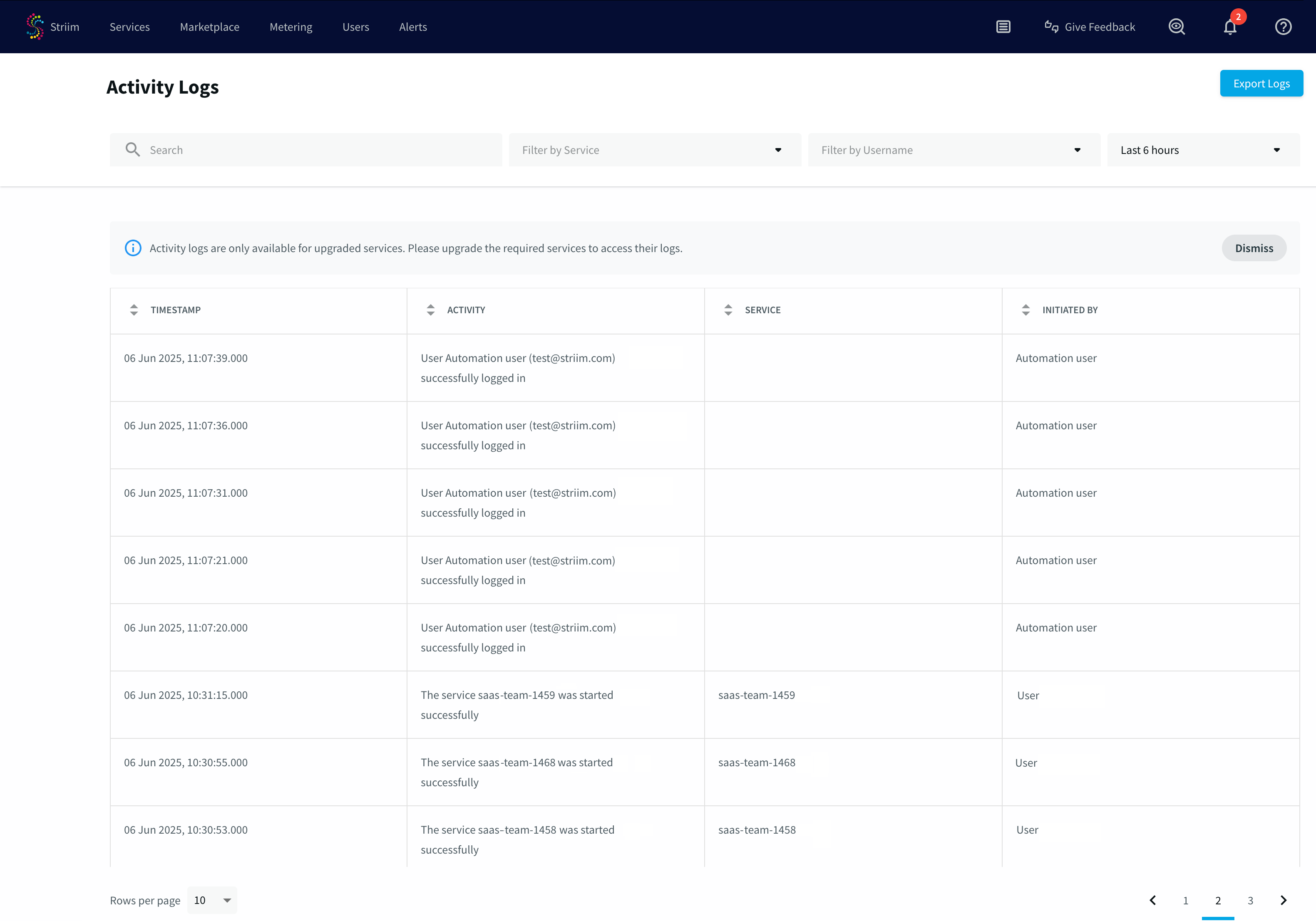
Account-level audit logs
Audit logs capture all user actions performed through the Striim Cloud UI. Each log entry includes the action type (e.g., Created, Updated, Deleted, Logged In, Logged Out), the user's identity (user ID, username, or email), the timestamp of the action (in UTC), and the affected service or entity.
These logs are immutable and stored securely to ensure tamper-proof integrity.
Audit logs provide a record of user actions across the service, including changes to services, network components, applications, user management, and authentication events. These logs help ensure transparency and accountability in user activity.
Audit information currently resides in two areas:
Control plane audit logs: These logs capture actions related to the lifecycle and management of services at the platform level.
Data plane command logs: These logs record all user-issued commands. They contribute to the overall audit trail by capturing direct interactions with the system.
Service-level audit logs
Service-level audit logs (also known as command logs) capture commands executed within the product, either through the console or via REST API requests. These logs appear in the activity log alongside account-level audit records and are part of the full audit trail. They provide traceability for configuration changes, data manipulation, and operational activity at the service level.
Filtering and managing log data
The Activity logs page includes several tools to help you navigate and analyze your log data efficiently:
Pagination: View large volumes of log entries in manageable pages, allowing quick access to earlier or later records.
Filtering: Narrow the displayed logs using filters for date range.
Search: Locate specific entries using keywords, entity names, or other searchable fields.
Export: Download activity log data as CSV files for external reporting or archiving.
Access control
Access to activity logs is governed by role-based access control (RBAC):
Admin users: Can view logs for all users within the account.
Service admin users: Can view logs for all users associated with services they manage.
Developer and viewer users: Can view only their own actions.
Read-only access: Users cannot modify or delete log entries.
Granular permissions: Visibility into logs can be further scoped by user or service context.
Security and integrity
Activity logs are designed to meet audit, compliance, and operational transparency needs. They are tamper-proof, securely stored, and cannot be altered by users. Activity logs are maintained for a minimum of one year.